|
 |
|||||||||||
|
||||||||||||
Notice: Undefined variable: cat in /hermes/walnacweb05/walnacweb05am/b834/hoc.caddea/computingsecurity/default.php on line 187
CODE RED! An essential guide to protecting your data
How should organisations minimise the likelihood that unauthorised code is able to manipulate...
How should organisations minimise the likelihood that unauthorised code is able to manipulate...
The Smoking Gun
Encryption is vital for protecting precious data. But, in the wrong hands, it can be a weapon that is...
Encryption is vital for protecting precious data. But, in the wrong hands, it can be a weapon that is...
The Exploitation Game
What steps can be taken to detect and block exploits as soon as they attempt to use software...
What steps can be taken to detect and block exploits as soon as they attempt to use software...
Sane strategies in risk-infested waters
What steps does any business have to take to get governance, risk and compliance right - and...
What steps does any business have to take to get governance, risk and compliance right - and...
Northamber out to shake up security market
With a newly launched solutions division and two security vendors just signed up, ...
With a newly launched solutions division and two security vendors just signed up, ...
Protecting your digital identity
Digital services are expanding rapidly, making the chances of identity theft an ever greater reality. ...
Digital services are expanding rapidly, making the chances of identity theft an ever greater reality. ...
Shadow IT – hassle and bliss for IT departments
‘Shadow IT’ divides companies into IT department and the rest of the people, getting businesses are off...
‘Shadow IT’ divides companies into IT department and the rest of the people, getting businesses are off...
Hand-to-hand combat
How concerned should businesses in the UK be about cyber assaults – are the attackers gaining...
How concerned should businesses in the UK be about cyber assaults – are the attackers gaining...
Success at InfoSec
Infosec 2015 bustled and thrived for three days in June at its new London base OF Olympia...
Infosec 2015 bustled and thrived for three days in June at its new London base OF Olympia...
EOL - Getting it right!
In a world where data proliferates – and is growing at a staggering rate...
In a world where data proliferates – and is growing at a staggering rate...
Single point of control
Identity and access management solutions - how much of a difference do they really make to an...
Identity and access management solutions - how much of a difference do they really make to an...
Defences put to the test
Penetration testing is a key weapon for establishing how secure networks, infrastructures...
Penetration testing is a key weapon for establishing how secure networks, infrastructures...
Cloud gets personal
BM has patented the design for a data privacy engine that can help businesses protect personal...
BM has patented the design for a data privacy engine that can help businesses protect personal...
The year ahead - what lies in wait?
2014 was a tumultuous 12 months: think only Heartbleed, Sony and JP Morgan Chase. 2015...
2014 was a tumultuous 12 months: think only Heartbleed, Sony and JP Morgan Chase. 2015...
Time to halt the Torrent
Stopping data leakage requires a robust chain of custody, with a high level of security, auditability and transparency...
Stopping data leakage requires a robust chain of custody, with a high level of security, auditability and transparency...
Crime fighters
Cyber threats to the UK remain a Tier-One national security risk. The need for highly skilled experts to help fight has never been so great...
Cyber threats to the UK remain a Tier-One national security risk. The need for highly skilled experts to help fight has never been so great...
Powerful Crossover
BM has made more than a dozen acquisitions in security over the past decade. Its latest, of Rome-based CrossIdeas, should prove....
BM has made more than a dozen acquisitions in security over the past decade. Its latest, of Rome-based CrossIdeas, should prove....
All-out Attack
Are Advanced Persistent Threats - APTs - getting out of control? A new report contains some stark findings....
Are Advanced Persistent Threats - APTs - getting out of control? A new report contains some stark findings....
Are you being properly served?
Managed security services are designed to help improve information security. but how well do they perform this function?....
Managed security services are designed to help improve information security. but how well do they perform this function?....
How safe is your quantified self?
Computing Security talks to Symantec's Orla Cox about the world of self-tracking, monitoring and wearable technology - and the issues....
Computing Security talks to Symantec's Orla Cox about the world of self-tracking, monitoring and wearable technology - and the issues....
Under Attack: Leading the Fightback
On the 31 March this year, the UK'S Cyber Emergency Response Team went live, in a bid to strengthen the country's online defences....
On the 31 March this year, the UK'S Cyber Emergency Response Team went live, in a bid to strengthen the country's online defences....
Human frailty
Most data breaches are the result of human mistakes, negligence or unexpected system glitches...
Most data breaches are the result of human mistakes, negligence or unexpected system glitches...
Why the Pen can be mightier than the sword
Penetration ('pen') testing is the practice of attacking your systems and network to seek out any vulnerabilities that others might try to exploit.
Penetration ('pen') testing is the practice of attacking your systems and network to seek out any vulnerabilities that others might try to exploit.
Raising the Standards
Launched in 2010, the Asset Disposal and Information Security Alliance (ADISA) has been busy working with a range of companies...
Launched in 2010, the Asset Disposal and Information Security Alliance (ADISA) has been busy working with a range of companies...
Security Directive Could Cost Organisations Billion
UK businesses could be hit hard in the pocket by a new EU Cyber Security Directive...
UK businesses could be hit hard in the pocket by a new EU Cyber Security Directive...
The Force that fights the cyber foes
The IBM X-Force Trend & Risk Report has been reporting on the alarming rate at which cyber attacks have continued to occur for some years now...
The IBM X-Force Trend & Risk Report has been reporting on the alarming rate at which cyber attacks have continued to occur for some years now...
Internal security breaches soar
Despite the widespread occurrence of the insider threat, only one in four I.T. professionals consider this to be a security priority
Despite the widespread occurrence of the insider threat, only one in four I.T. professionals consider this to be a security priority
315,000 new malicious files detected every day
The overall global Internet threat level has grown by 6.9 percentage points – during 2013, 41.6% of user computers were attacked..
The overall global Internet threat level has grown by 6.9 percentage points – during 2013, 41.6% of user computers were attacked..
BYOD - How to make it your friend
BYOD - bring your own device - is enjoying enormous growth and that is likely only to accelerate. However, opinion is still..
BYOD - bring your own device - is enjoying enormous growth and that is likely only to accelerate. However, opinion is still..
The data security divide
Barely a week goes by without yet another media report about a high-profile leak of confidential data.
Barely a week goes by without yet another media report about a high-profile leak of confidential data.
The Internet's Light And Dark Sides
While the internet is a positive force for good, it is also a haven for the very bad. And it doesn't get much worse than cybercrime..
While the internet is a positive force for good, it is also a haven for the very bad. And it doesn't get much worse than cybercrime..
Taking Phishing Off The Menu
Halon security's dmarc prevents attacks from spammers targeting spoof weaknesses
Halon security's dmarc prevents attacks from spammers targeting spoof weaknesses
Sun Shines On Cloud
The market for cloud, or Internet, computing is hitting the stratosphere. Market research firm IDC expects businesses worldwide..
The market for cloud, or Internet, computing is hitting the stratosphere. Market research firm IDC expects businesses worldwide..
Cold Shoulder Treatment
Many organisations are failing to adopt established industry best practice to protect their clients' information. The need for increased..
Many organisations are failing to adopt established industry best practice to protect their clients' information. The need for increased..
The CryptoFlow App from Certes Networks
Certes Networks has an enviable reputation in the data security world
Certes Networks has an enviable reputation in the data security world
Lepide Auditor Suite 15.2
Change auditing is an essential requirement for enterprises, helping them to comply with...
Change auditing is an essential requirement for enterprises, helping them to comply with...
Thycotic Secret Server
Privileged account credentials are the number one target for today's cyber criminals, as they...
Privileged account credentials are the number one target for today's cyber criminals, as they...
Titania PAWS Studio 2.4.4
SMBs that want to show compliance with data protection regulations will like Titania's PAWS Studio a lot
SMBs that want to show compliance with data protection regulations will like Titania's PAWS Studio a lot
Embrace a digital future!
Cyber Security Europe is returning to the ExCel London for the second year running in October this year...
Cyber Security Europe is returning to the ExCel London for the second year running in October this year...
Integral Memory Crypto SSD
It beggars belief that, even with all the publicity surrounding data protection, hardly a week goes by...
It beggars belief that, even with all the publicity surrounding data protection, hardly a week goes by...
macmon NAC
Network access control has traditionally had a mixed reception in enterprises, as all too many solutions...
Network access control has traditionally had a mixed reception in enterprises, as all too many solutions...
Titania TEC
UK-based Titania has a sharp focus on data security compliance and its latest TEC aims to make regulatory...
UK-based Titania has a sharp focus on data security compliance and its latest TEC aims to make regulatory...
Acunetix Online Vulnerability Scanner
In today's competitive global markets, SMBs need to protect their web sites from hackers ...
In today's competitive global markets, SMBs need to protect their web sites from hackers ...
Gemalto SafeNet ProtectV 2.0
The cost benefits alone make moving virtualised data centres into the cloud a no-brainer...
The cost benefits alone make moving virtualised data centres into the cloud a no-brainer...
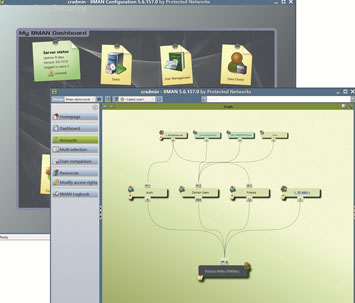
8MAN: from protected-networks.com
A fundamental requirement for meeting compliance regulations is Active Directory (AD...
A fundamental requirement for meeting compliance regulations is Active Directory (AD...
The CR35iNG security appliance...
Cyberoam's latest NG Series of security appliances set themselves apart from the competition, as they deliver....
Cyberoam's latest NG Series of security appliances set themselves apart from the competition, as they deliver....
Celestix Networks HOTPin v3.7
The exponential growth of mobile workforces is making businesses rethink their security strategy for remote access...
The exponential growth of mobile workforces is making businesses rethink their security strategy for remote access...
GFI WirelessSentry
GFI's WirelessSentry (WiSe) takes the expense out of wireless network monitoring by uniquely offering it as a cloud service
GFI's WirelessSentry (WiSe) takes the expense out of wireless network monitoring by uniquely offering it as a cloud service
ManageEngine EventLog Analyzer
ManageEngine's EventLog Analyzer (MEA) offers an interesting alternative to the mainstream SIEM (security information and event management)...
ManageEngine's EventLog Analyzer (MEA) offers an interesting alternative to the mainstream SIEM (security information and event management)...
Celestix Networks' HOTPin v3.7
The exponential growth of mobile workforces is making businesses rethink their security strategy for remote access...
The exponential growth of mobile workforces is making businesses rethink their security strategy for remote access...
GFI LanGuard 2014
Focusing on endpoint vulnerability assessment, patch management and auditing...
Focusing on endpoint vulnerability assessment, patch management and auditing...
SecurEnvoy SecurAccess 7.1
The use of two-factor authentication (2FA) for online security is growing exponentially as businesses move away from inherently...
The use of two-factor authentication (2FA) for online security is growing exponentially as businesses move away from inherently...
SolarWinds Log & Event Manager
Despite the wide choice of SIEM (security information and event management) solutions, their high prices put most of them..
Despite the wide choice of SIEM (security information and event management) solutions, their high prices put most of them..
AhnLab Malware Defense System
Currently the largest security company in South Korea, AhnLab now turns it gaze on the European market. Having dealt efficiently...
Currently the largest security company in South Korea, AhnLab now turns it gaze on the European market. Having dealt efficiently...
Titania Nipper Studio
Total compliance with data protection regulations is now essential, otherwise businesses could find themselves....
Total compliance with data protection regulations is now essential, otherwise businesses could find themselves....
CenterTools DriveLock Executive Suite 7.2
Data loss and security breaches are rarely out of the news, showing that, despite all the warnings...
Data loss and security breaches are rarely out of the news, showing that, despite all the warnings...
Understanding the differences between antivirus and anti-malware
Seeking the best way to reducing your attack surface? First, you need to understand the...
Seeking the best way to reducing your attack surface? First, you need to understand the...
Protecting applications from Firewall failure
How to protect applications, in the context of changing network access and a porous perimeter...
How to protect applications, in the context of changing network access and a porous perimeter...
PSN-compliant mobile working
A PSN-compliant mobile working solution offers tangible benefits, but it is critical to enter into the process with a robust strategy...
A PSN-compliant mobile working solution offers tangible benefits, but it is critical to enter into the process with a robust strategy...
In pursuit of radical change
Tim Ager of Celestix has been working closely with local and regional government organisations to....
Tim Ager of Celestix has been working closely with local and regional government organisations to....
Security? It's in Microsoft's DNA!
While many rue what they see as the disappearance of Microsoft from the security business...
While many rue what they see as the disappearance of Microsoft from the security business...
Can cyber-risk insurance really keep you safe?
Cyber-risk insurance policies are growing in popularity with the business community, but there’s a danger...
Cyber-risk insurance policies are growing in popularity with the business community, but there’s a danger...
Why Windows 8 is so gr8!
Tim Ager says the demise of Windows xp is no cause for lamentation - Windows 8 has so much to offer...v
Tim Ager says the demise of Windows xp is no cause for lamentation - Windows 8 has so much to offer...v
2014: Into The Unknown
We need to keep evolving ways in which to authenticate our trusted users, if we are to stay ahead...
We need to keep evolving ways in which to authenticate our trusted users, if we are to stay ahead...
Managing The Risks
Risk-based authentication is now making its presence felt. Tim Ager of Celestix explains why and what it is all about...
Risk-based authentication is now making its presence felt. Tim Ager of Celestix explains why and what it is all about...
Key factors in a mobile world
As mobile device management becomes an ever greater challenge, its convergence with two-factor authentication...
As mobile device management becomes an ever greater challenge, its convergence with two-factor authentication...
‘Anonymity’ software leaks users’ details
It's alarming to hear that the services used by hundreds of thousands of people – legitimately to protect...
It's alarming to hear that the services used by hundreds of thousands of people – legitimately to protect...
GDPR - coming, ready or not!
According to a new survey by iStorage, almost a third of public and private sector professionals are not aware...
According to a new survey by iStorage, almost a third of public and private sector professionals are not aware...
Fears and deaf ears
Would you consider stripping your employees of company smart phones and memory sticks to protect your...
Would you consider stripping your employees of company smart phones and memory sticks to protect your...
Anthem for cyber victims
Following the recent Anthem breach – where the USA's second largest health insurer was hacked...
Following the recent Anthem breach – where the USA's second largest health insurer was hacked...
'Tails' of the unexpected?
No new year can ever come along without a wealth of security predictions already hanging...
No new year can ever come along without a wealth of security predictions already hanging...
KGB, Stasi... and now the UK government?
A research report published by F-Secure shows the growing concern of the British public with mass surveillance being undertaken by the British government on its own people, as well as foreign nationals
A research report published by F-Secure shows the growing concern of the British public with mass surveillance being undertaken by the British government on its own people, as well as foreign nationals
Sigh... sigh...Cyber: Paying the price
Sigh... sigh...Cyber: Paying the price
Sigh... sigh...Cyber: Paying the price
Urgent need to boost cyber skills
Businesses must do far more to tackle cybercrime, which is threatening to spiral out of control...
Businesses must do far more to tackle cybercrime, which is threatening to spiral out of control...
Don't let it all end in floods of tears
Water has been constantly in the headlines of late, infiltrating communities on a massive scale and leaving a trail of destruction in its wake
Water has been constantly in the headlines of late, infiltrating communities on a massive scale and leaving a trail of destruction in its wake
Inside 2014
Ask those in the know what will be the hot topics for security in 2014 and there is no shortage of response...
Ask those in the know what will be the hot topics for security in 2014 and there is no shortage of response...
Massive strides forward
If there is one thing that the 2013 Computing Security Awards demonstrated above all else, it's the fact that the industry...
If there is one thing that the 2013 Computing Security Awards demonstrated above all else, it's the fact that the industry...
Data Breaches - Time To Come Clean
The day that telecoms operators and internet service providers (ISPs) across Europe must have dreaded has finally arrived...
The day that telecoms operators and internet service providers (ISPs) across Europe must have dreaded has finally arrived...
Anxious times signal need for action
The Intelligence and Security Committee (ISC) of Parliament has just published its Annual Report for 2012-2013...
The Intelligence and Security Committee (ISC) of Parliament has just published its Annual Report for 2012-2013...
British gas hack sparks warning
In the wake of the recent news that the email addresses and account passwords of 2,200 British...
In the wake of the recent news that the email addresses and account passwords of 2,200 British...
Complaints from public soar
The Information Commissioners Office (ICO) has received a record number of complaints from ...
The Information Commissioners Office (ICO) has received a record number of complaints from ...
Traditional defences are simply not enough
"In today's more vulnerable, distributed network environments, firewalls and antivirus are...
"In today's more vulnerable, distributed network environments, firewalls and antivirus are...
Data-centric model is ‘the key to our security’
Dietrich Benjes, director UK, Ireland and Middle East at Varonis has commented on the recent speech...
Dietrich Benjes, director UK, Ireland and Middle East at Varonis has commented on the recent speech...
Certes announces SOTI alliance
Certes Networks has recently announced a partnership with SOTI, a provider of enterprise mobility...
Certes Networks has recently announced a partnership with SOTI, a provider of enterprise mobility...
Maladjusted to Malvertising
Malvertising - when malicious content attempts to infect a PC through one of the ads on a website - is ...
Malvertising - when malicious content attempts to infect a PC through one of the ads on a website - is ...
GOVSEC event is a winner
Whitehall Media's recent Government IT Security & Risk Management conference at the Hotel Russell...
Whitehall Media's recent Government IT Security & Risk Management conference at the Hotel Russell...
Cybercrime has now emerged as Enemy No.1
Cybercrime has formally emerged as the single largest type of offence in the UK following the reclassification of...
Cybercrime has formally emerged as the single largest type of offence in the UK following the reclassification of...
Lancaster University seals strategic research partnership
Lancaster University has agreed a strategic research partnership with Nettitude - a provider of cyber...
Lancaster University has agreed a strategic research partnership with Nettitude - a provider of cyber...
First UK cyber academy graduates head toward recruitment
The first 30 students of the UK Cyber Academy - SANS' 8-week, residential cyber security training...
The first 30 students of the UK Cyber Academy - SANS' 8-week, residential cyber security training...
Varonis announces interoperability with HP ArcSite
Customers To Gain Unprecedented Intelligence About Their Vast Stores of Unstructured Data
Customers To Gain Unprecedented Intelligence About Their Vast Stores of Unstructured Data
Kroll Ontrack reports that it is receiving a growing number...
While ransomware is not new, attacks have tended to focus in the past on home and small business...
While ransomware is not new, attacks have tended to focus in the past on home and small business...
Manufacturers ‘wide open to attack’
Manufacturers are leaving themselves wide open to attack from bad actors....
Manufacturers are leaving themselves wide open to attack from bad actors....
'Inspired' take on skills shortage
A new website has been unveiled that aims to help address the cyber security skills shortage by...
A new website has been unveiled that aims to help address the cyber security skills shortage by...
Warning issued over new wave of botnets
Researchers at Raytheon|Websense are urging businesses to be on their guard against a new wave...
Researchers at Raytheon|Websense are urging businesses to be on their guard against a new wave...
Dyre straits as bank customers hit
Norton by Symantec has released new research on the Dyre Trojan, which is now configured to defraud...
Norton by Symantec has released new research on the Dyre Trojan, which is now configured to defraud...
Dell SecureWorks for Edinburgh
Dell SecureWorks has announced the opening of a new facility in Edinburgh
Dell SecureWorks has announced the opening of a new facility in Edinburgh
Opening a window on Microsoft vulnerabilities
Microsoft Windows' popularity has always made it an attractive target for cybercriminals...
Microsoft Windows' popularity has always made it an attractive target for cybercriminals...
Partnership deal takes off
Etihad Airways and Okta have announced a strategic technology partnership to integrate Okta's...
Etihad Airways and Okta have announced a strategic technology partnership to integrate Okta's...
Privileged access management
WALLIX has announced what it claims is the world's first on-demand solution for privileged access management...
WALLIX has announced what it claims is the world's first on-demand solution for privileged access management...
Commitment to excellence recognised with new standard
Sims Recycling Solutions is amongst the first organisations to be awarded the CAS-S...
Sims Recycling Solutions is amongst the first organisations to be awarded the CAS-S...
Students learn skills to fight cybercrime
Undergraduates from the University of Northampton are being equipped with the skills to fight on...
Undergraduates from the University of Northampton are being equipped with the skills to fight on...
CoSoSys in move to secure Macs
CoSoSys has now released Mobile Device Management (MDM) features for OS X. ...
CoSoSys has now released Mobile Device Management (MDM) features for OS X. ...
WALLIX launches WAB On Demand
WALLIX launches offering dedicated to privileged access management on demand
WALLIX launches offering dedicated to privileged access management on demand
PhishMe enhances Triage's real-time malicious file analysis and notification
PhishMe has announced enhancements to its PhishMe Triage product, which leverages human intelligence to provide...
PhishMe has announced enhancements to its PhishMe Triage product, which leverages human intelligence to provide...
Are employees letting phishing attacks off the hook?
A survey of over 200 IT professionals carried out at this year’s InfoSecurity Europe has found that, ...
A survey of over 200 IT professionals carried out at this year’s InfoSecurity Europe has found that, ...
Crime-busting academy unveiled
A new crime-busting International Cyber Academy has been launched
A new crime-busting International Cyber Academy has been launched
Symantec names new VP & MD FOR Northern Europe
Symantec has further strengthened its growth by appointing industry veteran Keith Bird as vice president...
Symantec has further strengthened its growth by appointing industry veteran Keith Bird as vice president...
Average cost of a data breach soars to £2.37 million
Latest research from The Ponemon Institute in association with IBM has found that the average cost of a data...
Latest research from The Ponemon Institute in association with IBM has found that the average cost of a data...
Ethical hacking under scrutiny
The UK cyber security industry would benefit from increased standardisation of widespread 'penetration testing'...
The UK cyber security industry would benefit from increased standardisation of widespread 'penetration testing'...
Advanced integration with cloud storage apps
CoSoSys has announced the development of Endpoint Protector 4 to include new integrations with Dropbox...
CoSoSys has announced the development of Endpoint Protector 4 to include new integrations with Dropbox...
Time to stem the breach
Research conducted by AlienVault has shown that 20% of IT security professionals have witnessed a breach being hidden or covered up
Research conducted by AlienVault has shown that 20% of IT security professionals have witnessed a breach being hidden or covered up
Huge increase in malware
Check Point's 2015 Security Report
Check Point's 2015 Security Report
UK lags behind Germany in patching ability
A survey of 200 UK and 200 German organisations, conducted by Vanson Bourne on behalf of Tenable Network Security...
A survey of 200 UK and 200 German organisations, conducted by Vanson Bourne on behalf of Tenable Network Security...
Data at the mercy of hackers as breaches go undetected
A survey conducted by LogRhythm has revealed 46% of organisations that suffered a data breach...
A survey conducted by LogRhythm has revealed 46% of organisations that suffered a data breach...
Europe's No.1 Information Security Conference and Exhibition
‘Intelligent Security: Protect. Detect. Respond. Recover.’ is the theme of Infosecurity Europe 2015...
‘Intelligent Security: Protect. Detect. Respond. Recover.’ is the theme of Infosecurity Europe 2015...
Phoenix survey reveals full extent of BYOD threat
Around 60% of BYOD workers do not involve their company's IT support in setting up their devices
Around 60% of BYOD workers do not involve their company's IT support in setting up their devices
85,000 new malicious IPS a day
The new Webroot 2015 Threat Brief reveals that 85,000 new malicious IPs...
The new Webroot 2015 Threat Brief reveals that 85,000 new malicious IPs...
New research highlights worrying lack of mobile app security
IBM Security and the Ponemon Institute have released new research unveiling...
IBM Security and the Ponemon Institute have released new research unveiling...
Senior management must tackle the insider threat
More than half of IT professionals (57%) believe their organisation's senior management ...
More than half of IT professionals (57%) believe their organisation's senior management ...
Staying ahead of threats
AlienVault is to work with HP to broaden the reach of cyber threat intelligence sharing...
AlienVault is to work with HP to broaden the reach of cyber threat intelligence sharing...
Lack of confidence in data security measures
New research released by IT analyst firm Quocirca, in conjunction with Digital Guardian...
New research released by IT analyst firm Quocirca, in conjunction with Digital Guardian...
Breached in just 82 seconds
A startling finding in this year's Verizon's Data Breach Investigations Report is that, in 60% of breaches...
A startling finding in this year's Verizon's Data Breach Investigations Report is that, in 60% of breaches...
ATD foresight from ForeScout
ForeScout has announced new ControlFabric integrations with several industry-leading advanced...
ForeScout has announced new ControlFabric integrations with several industry-leading advanced...
Symantec Names New Executive Leadership Team
Since announcing its plan to separate into two publicly traded companies
Since announcing its plan to separate into two publicly traded companies
Privileged account management put to the test
A report by a leading industry analyst firm has stated that there are five key solution...
A report by a leading industry analyst firm has stated that there are five key solution...
New Cryptzone survey reveals...
Report finds inside threats pose highest risk, and security budgets slow to increase...
Report finds inside threats pose highest risk, and security budgets slow to increase...
Invisible infrastructure and access management...
AppGate Secure Access Enables Organizations to Adopt Software Defined Perimeter Approach...
AppGate Secure Access Enables Organizations to Adopt Software Defined Perimeter Approach...
HP highlights biggest threats
HP has released its sixth annual 'Cyber Risk Report'
HP has released its sixth annual 'Cyber Risk Report'
Make sure your workforce is savvy...
BCS, The Chartered Institute for IT, is calling on businesses to ensure their employees...
BCS, The Chartered Institute for IT, is calling on businesses to ensure their employees...
Banking Malware Detector
Software security company Minded Security is launching in the UK to combat hidden banking threats and, it states...
Software security company Minded Security is launching in the UK to combat hidden banking threats and, it states...
New Infosec course launched for I.T...
April will see the UK's first ever hands-on InfoSec course designed specifically for IT...
April will see the UK's first ever hands-on InfoSec course designed specifically for IT...
IT security takes a Step Up
According to a new 'Data Protection Maturity' study released by Lumension, IT security departments are...
According to a new 'Data Protection Maturity' study released by Lumension, IT security departments are...
Soft target for Assailants
The Internet of Things (IoT) is becoming a soft target for cyber attacks, according to the 2015...
The Internet of Things (IoT) is becoming a soft target for cyber attacks, according to the 2015...
New name, new vision
Symantec has announced Veritas Technologies Corporation as the name for its independent publicly...
Symantec has announced Veritas Technologies Corporation as the name for its independent publicly...
UK University strikes research deal with Japan...
Lancaster University is enhancing its position as a global leader in cyber security research...
Lancaster University is enhancing its position as a global leader in cyber security research...
Cyber threat fuels I.T. graduate recruitment drive
Reflecting the increasing threat from cybercrime, whether by individual threat actors or nation state...
Reflecting the increasing threat from cybercrime, whether by individual threat actors or nation state...
Fears raised over employee password sell-off
Following the discovery by SailPoint that UK workers would be willing to sell their passwords...
Following the discovery by SailPoint that UK workers would be willing to sell their passwords...
Key security trends of 2014
IT security provider Trend Micro has released its 2014 Annual Security Roundup
IT security provider Trend Micro has released its 2014 Annual Security Roundup
Widespread data concerns
As data issues around loss, theft or surveillance continue to hit the headlines, data privacy now...
As data issues around loss, theft or surveillance continue to hit the headlines, data privacy now...
Fears stop firms using cloud computing
New research from the Federation of Small Businesses (FSB) has found that, despite 60% of small firms...
New research from the Federation of Small Businesses (FSB) has found that, despite 60% of small firms...
Wick Hill gains cyber essentials certification
Wick Hill has gained the recently launched Government Cyber Essentials certification...
Wick Hill has gained the recently launched Government Cyber Essentials certification...
Give01Day and IASME to secure all UK charities with UK...
Give01Day has joined forces with the Government’s Cyber Streetwise campaign and the IASME...
Give01Day has joined forces with the Government’s Cyber Streetwise campaign and the IASME...
Combatting the insider threat
According to recent reports, Morgan Stanley has joined the growing list of worldwide firms...
According to recent reports, Morgan Stanley has joined the growing list of worldwide firms...
Don’t get left on the shelf!
Trustwave has released new data about the 'shelfware' problem that plagues businesses of all sizes
Trustwave has released new data about the 'shelfware' problem that plagues businesses of all sizes
'Selfies' that aim to catch out device thieves
Certificate authority and internet security organisation Comodo has released Comodo Mobile...
Certificate authority and internet security organisation Comodo has released Comodo Mobile...
New malware unlocks corporate defences for hackers
Dell SecureWorks' Counter Threat Unit (CTU) researchers have discovered malware that allows hackers...
Dell SecureWorks' Counter Threat Unit (CTU) researchers have discovered malware that allows hackers...
Cyber crime soars up the risk barometer
Businesses face new challenges from a rise of disruptive scenarios in an...
Businesses face new challenges from a rise of disruptive scenarios in an...
BAE Systems' silver lining
BAE Systems has completed the acquisition of Perimeter Internetworking Corp, which...
BAE Systems has completed the acquisition of Perimeter Internetworking Corp, which...
What time is the hack due?
Following the news that cyber terrorists hacked Bristol bus timetable site TravelWest
Following the news that cyber terrorists hacked Bristol bus timetable site TravelWest
New infosecurity conference
Infosecurity Europe, the specialist information security conference and exhibition, is launching...
Infosecurity Europe, the specialist information security conference and exhibition, is launching...
What keeps digital leaders awake at night?
Security, loss of data and cloud security are the top things that keep digital leaders...
Security, loss of data and cloud security are the top things that keep digital leaders...
Temporary workers handed administrative privileges
Some 72% of temporary workers admit to being given administrative...
Some 72% of temporary workers admit to being given administrative...
Cyber security masters, Online
A new online master's degree in cyber security, launched by Coventry University...
A new online master's degree in cyber security, launched by Coventry University...
$710M move to snare Tripwire
An agreement to purchase cyber security company Tripwire for US$710 million has...
An agreement to purchase cyber security company Tripwire for US$710 million has...
Impact of sony hack widens as...
In the wake of the massive highly publicised hack against Sony that reverberated...
In the wake of the massive highly publicised hack against Sony that reverberated...
Global push for better cyber security...
A global online resource for building cyber security capacity has been launched.
A global online resource for building cyber security capacity has been launched.
Cyber Essentials Scheme will have pivotal role...
Organisations should prepare for the increased threat of targeted cyber-attacks in 2015 by reviewing their security polices in alignment with the government’s Cyber Essentials Scheme (CES)
Organisations should prepare for the increased threat of targeted cyber-attacks in 2015 by reviewing their security polices in alignment with the government’s Cyber Essentials Scheme (CES)
Cyber-security collaboration group announced
A strategic collaboration group has been formed to explore cyber-security for connected vehicles, amongst other key issues
A strategic collaboration group has been formed to explore cyber-security for connected vehicles, amongst other key issues
Innovative IT Asset Management Services
Sims Recycling Solutions’ 5-year strategic plan outlines comprehensive reuse and recycling services
Sims Recycling Solutions’ 5-year strategic plan outlines comprehensive reuse and recycling services
Computing Security Awards 2014 - the winners!
The 2014 Computing Security Awards culminated with an awards ceremony on October 9th. at the Hotel...
The 2014 Computing Security Awards culminated with an awards ceremony on October 9th. at the Hotel...
New EU Data Protection reforms...
The EU is to impose new data protection legislation to ensure better protection of the personal information....
The EU is to impose new data protection legislation to ensure better protection of the personal information....
Enterprises at risk
Websense has unveiled new findings from the global Ponemon Institute survey, 'Roadblocks, Refresh....
Websense has unveiled new findings from the global Ponemon Institute survey, 'Roadblocks, Refresh....
175 Million plus customer reords compromised
SafeNet, a global leader in data protection solutions, has released the highlights from its SafeNet....
SafeNet, a global leader in data protection solutions, has released the highlights from its SafeNet....
New App for safer interaction
Comodo has released a desktop application that enables users to safely interact with mission-critical...
Comodo has released a desktop application that enables users to safely interact with mission-critical...
Partnership to Deliver Critical Incident Response
Guidance Software is partnering with Thales to deliver a full range of endpoint security...
Guidance Software is partnering with Thales to deliver a full range of endpoint security...
Rise of the Cybervors
Hold Security has identified a Russian cyber gang now in possession of what it says is the largest cache of stolen data ever.
Hold Security has identified a Russian cyber gang now in possession of what it says is the largest cache of stolen data ever.
European Central Bank hack...
Cybercriminals often act within communities and this is a likely scenario with the recent attack....
Cybercriminals often act within communities and this is a likely scenario with the recent attack....
UK Business data at risk
New research released shows UK business data at risk as a result of haphazard and cavalier ....
New research released shows UK business data at risk as a result of haphazard and cavalier ....
Kaseya acquires Scorpion Software
Kaseya has acquired Scorpion Software, providers of integrated two factor authentication, single sign on and password management solutions.
Kaseya has acquired Scorpion Software, providers of integrated two factor authentication, single sign on and password management solutions.
Faulty towers?
The U.S Secret Service has given out advice to those in the hospitality industry to inspect computers which they make available to guests...
The U.S Secret Service has given out advice to those in the hospitality industry to inspect computers which they make available to guests...
Poor password management...
IT security professionals are gambling with the security of their organisations by failing to update important service and process account passwords on a regular basis...
IT security professionals are gambling with the security of their organisations by failing to update important service and process account passwords on a regular basis...
UKFast CEO pledges £1m...
The CEO of cloud and hosting firm UKFast has pledged £1m to keeping businesses safe online
The CEO of cloud and hosting firm UKFast has pledged £1m to keeping businesses safe online
Sophos challenges UK public...
Sophos is calling on members of the UK public to turn sleuth and to investigate confiscated crime scene computer systems...
Sophos is calling on members of the UK public to turn sleuth and to investigate confiscated crime scene computer systems...
Getting to grips with The Internet of Things
GFI Software has announced the findings of an extensive independent research project examining the “Internet of Things” (IoT)...
GFI Software has announced the findings of an extensive independent research project examining the “Internet of Things” (IoT)...
Databarracks certified for government's...
Databarracks has been named as one of the first organisations in the UK to become certified with the Cyber Essentials Scheme...
Databarracks has been named as one of the first organisations in the UK to become certified with the Cyber Essentials Scheme...
Cybercrime responsible for more than £266bn...
A new report from the Center for Strategic and International Studies (CSIS) and sponsored by McAfee, “Net Losses – Estimating the Global Cost of Cybercrime,...
A new report from the Center for Strategic and International Studies (CSIS) and sponsored by McAfee, “Net Losses – Estimating the Global Cost of Cybercrime,...
AlienVault releases new version of Open Threat Exchange
AlienVault has released an updated version of Open Threat Exchange (OTX), which includes OTTX ThreatFinder...
AlienVault has released an updated version of Open Threat Exchange (OTX), which includes OTTX ThreatFinder...
CBEST foot forward for banking?
Geoff Webb, senior director, solution strategy at NetIQ, comments on the Bank of England's new cybercrime testing framework, CBEST.
Geoff Webb, senior director, solution strategy at NetIQ, comments on the Bank of England's new cybercrime testing framework, CBEST.
Tier-3 is early adopter of UK “Cyber Essentials” standard
Tier-3 has become one of the first adopters of the new UK Cyber Essentials standard, which has been produced by the Department for Business...
Tier-3 has become one of the first adopters of the new UK Cyber Essentials standard, which has been produced by the Department for Business...
Celestix networks seeks out an Edge
Celestix Networks has recently launched its new Cloud Edge Security Appliance series to enable secure and seamless connectivity...
Celestix Networks has recently launched its new Cloud Edge Security Appliance series to enable secure and seamless connectivity...
Macro Malware: An Unexpected Return
The re-emergence of macro malware after more than 10 years, when it seemed to have died out, ...
The re-emergence of macro malware after more than 10 years, when it seemed to have died out, ...
The Changing Compliance Landscape: Going Circular
By Anand Narasimhan, director UK, EU & NI, Sims Recycling Solutions
By Anand Narasimhan, director UK, EU & NI, Sims Recycling Solutions
Tipping the balance!
How do you best manage the upwardly mobile workforce? Patrick Warley, Global Head of Research...
How do you best manage the upwardly mobile workforce? Patrick Warley, Global Head of Research...
Top 3 data security threats
Roman Foeckl, CEO and founder of CoSoSys, offers his insights on how to mitigate...
Roman Foeckl, CEO and founder of CoSoSys, offers his insights on how to mitigate...
Navigating the forest of security certifications
Patrick Warley, global head of research & development at Integral Memory...
Patrick Warley, global head of research & development at Integral Memory...
So far, so good...
In our last issue, we highlighted the likely threats that will hit organisations across the UK in the 12 months...
In our last issue, we highlighted the likely threats that will hit organisations across the UK in the 12 months...
Technologies to keep you safe
With attacks increasing in frequency and sophistication, which are the technologies...
With attacks increasing in frequency and sophistication, which are the technologies...
Massive Attacks - We're Still in Denial
The enterprise perimeter does not exist anymore - and a much more proactive approach to security is needed, says Bill Strain, CTO of cloud company iomart.
The enterprise perimeter does not exist anymore - and a much more proactive approach to security is needed, says Bill Strain, CTO of cloud company iomart.
Enough to make your pulse soar
Imagine this scenario: Monitoring programmers' pulses, their eye movements and even anxiety levels to detect when they could be in trouble.
Imagine this scenario: Monitoring programmers' pulses, their eye movements and even anxiety levels to detect when they could be in trouble.
Taking the next step up
The industry needs to move towards a more holistic view of information and systems, argues Dr Anand Narasimhan, director, Sims Lifecycle Services EU
The industry needs to move towards a more holistic view of information and systems, argues Dr Anand Narasimhan, director, Sims Lifecycle Services EU
Security’s second chance
By Terry Greer-King, Director of Cyber Security, Cisco.
By Terry Greer-King, Director of Cyber Security, Cisco.
‘Advanced threat detection is more than a moment in time’
By Sean Newman, Security Strategist, Sourcefire, now part of Cisco.
By Sean Newman, Security Strategist, Sourcefire, now part of Cisco.
Anti-Virus, the Cloudmark way
Is there any way to defend against malware that is undetectable...
Is there any way to defend against malware that is undetectable...
Beyond Antivirus
Comodo's Melih Abdulhayoglu explains his company's unique approach to sandboxing and the...
Comodo's Melih Abdulhayoglu explains his company's unique approach to sandboxing and the...
Becoming an APT Spycatcher
Cybercrime has become somewhat 'old school' in its approach today, writes Andy Travers, VP EMEA at....
Cybercrime has become somewhat 'old school' in its approach today, writes Andy Travers, VP EMEA at....
Malware: Coming Soon to Your Company?
As the malware threat evolves, businesses need to rethink their methods of protection.
As the malware threat evolves, businesses need to rethink their methods of protection.
Staying safe in the mobile world
By Sean Newman, Security Strategist, Cisco....
By Sean Newman, Security Strategist, Cisco....
the great myth about mobile security
By Mark Reeves, SVP International for Entrust.
By Mark Reeves, SVP International for Entrust.
Plaudits for the PCI audits
Ian Whiting, CEO at Titania, offers his insights on PCI-DSS Compliance - and important changes that have now emerged for Pen Testers
Ian Whiting, CEO at Titania, offers his insights on PCI-DSS Compliance - and important changes that have now emerged for Pen Testers
Endpoint Security: A Call to Action
In a world of constant combat between hackers and security practitioners, corporate IT teams must continually strengthen their IT security...
In a world of constant combat between hackers and security practitioners, corporate IT teams must continually strengthen their IT security...
Raising the standard for cyber security is vital
Organisations will now have to meet a rigorous new cyber security 'kitemark' if they want to work with the UK government
Organisations will now have to meet a rigorous new cyber security 'kitemark' if they want to work with the UK government
Securing the Mobility Age through the Cloud
Employee mobility will be the rule, rather than the exception, in 2014. Michael Sutton, VP of security research at Zscaler, explains why
Employee mobility will be the rule, rather than the exception, in 2014. Michael Sutton, VP of security research at Zscaler, explains why
Tackling the fraudsters
Fraud is on the rise. Wherever you surf, tweet or otherwise go online, it rears its devious and lucrative head..
Fraud is on the rise. Wherever you surf, tweet or otherwise go online, it rears its devious and lucrative head..
The security challenges ahead for 2014
Tim 'TK' Keanini, CTO at Lancope, has put together his thoughts on some promising, as well as some concerning, innovations that will shape the way we secure..
Tim 'TK' Keanini, CTO at Lancope, has put together his thoughts on some promising, as well as some concerning, innovations that will shape the way we secure..
Computing Security Awards 2015
Excellence Shines Through
Excellence Shines Through
Anti Spam Solution of the Year – Computing Security 2015
WINNER: Libra ESVA - Libra ESVA
WINNER: Libra ESVA - Libra ESVA
Anti Malware Solution of the Year – Computing Security 2015
WINNER: ThreatTrack - VIPRE
WINNER: ThreatTrack - VIPRE
Content Security Solution of the Year – Computing Security 2015
WINNER: FuseMail - WebSMART
WINNER: FuseMail - WebSMART
Network Security Solution of the Year – Computing Security 2015
WINNER: Titania - Nipper Studio
WINNER: Titania - Nipper Studio
Encryption Solution of the Year – Computing Security 2015
WINNER: Integral Memory - Crypto SSD
WINNER: Integral Memory - Crypto SSD
DLP Solution of the Year – Computing Security 2015
WINNER: CoSoSys - EndPoint Protector 4
WINNER: CoSoSys - EndPoint Protector 4
Mobile Security Solution of the Year – Computing Security 2015
WINNER: Good Technology - Good Work
WINNER: Good Technology - Good Work
Identity and Access Management Solution of the Year – Computing Security 2015
WINNER: ForgeRock - Open AM
WINNER: ForgeRock - Open AM
Auditing / Reporting Solution of the Year – Computing Security 2015
WINNER: Fortinet - FortiAnalyzer
WINNER: Fortinet - FortiAnalyzer
Network Access Control Solution of the Year – Computing Security 2015
WINNER: macmon - macmon NAC
WINNER: macmon - macmon NAC
Cloud Security Solution of the Year – Computing Security 2015
WINNER: Egress - Egress Switch
WINNER: Egress - Egress Switch
Messaging Security Solution of the Year – Computing Security 2015
WINNER: GFI Software - GFI MailEssentials
WINNER: GFI Software - GFI MailEssentials
Advanced Persistent Threat (APT) Solution of the Year – Computing Security 2015
WINNER: AlienVault - Unifed Security Management
WINNER: AlienVault - Unifed Security Management
Secure Data Erasure Company of the Year – Computing Security 2015
WINNER: Sims Recycling Solutions
WINNER: Sims Recycling Solutions
Security Recruitment Company of the Year – Computing Security 2015
WINNER: Evolution Recruitment Solutions
WINNER: Evolution Recruitment Solutions
Security Service Provider of the Year – Computing Security 2015
WINNER: ZeroDayLab
WINNER: ZeroDayLab
SME Security Solution of the Year – Computing Security 2015
WINNER: WatchGuard - M300
WINNER: WatchGuard - M300
Enterprise Security Solution of the Year – Computing Security 2015
WINNER: Darktrace - Enterprise Immune System
WINNER: Darktrace - Enterprise Immune System
Security Project of the Year - Public Sector – Computing Security 2015
WINNER: Cafcass/Egress
WINNER: Cafcass/Egress
Security Project of the Year - Private Sector - Financial Services – Computing Security 2015
WINNER: Barclays / Good Technology
WINNER: Barclays / Good Technology
Security Project of the Year - Private Sector - General – Computing Security 2015
WINNER: Institute of Marine Engineering / Libra ESVA
WINNER: Institute of Marine Engineering / Libra ESVA
Editor’s Choice – Computing Security 2015
WINNER: Celestix - CelestixEdge E Series Appliance
WINNER: Celestix - CelestixEdge E Series Appliance
Security Distributor of the Year – Computing Security 2015
WINNER: Wick Hill
WINNER: Wick Hill
Security Reseller of the Year – Computing Security 2015
WINNER: Brookcourt
WINNER: Brookcourt
New Product of the Year – Computing Security 2015
WINNER: Celestix - CelestixEdge E Series Appliance
WINNER: Celestix - CelestixEdge E Series Appliance
Personal Contribution to IT Security Award – Computing Security 2015
WINNER: Corey Nachreiner
WINNER: Corey Nachreiner
Security Company of the Year – Computing Security 2015
WINNER: Titania
WINNER: Titania
Anti Spam Solution of the Year - Security 2014
WINNER: Libra Esva - Libra Esva Libra Esva triumphed in the Anti Spam category, with Paolo Frizzi accepting the award
WINNER: Libra Esva - Libra Esva Libra Esva triumphed in the Anti Spam category, with Paolo Frizzi accepting the award
Anti Malware Solution of the Year - Security 2014
WINNER: Comodo - ESM Comodo won the Anti Malware Solution of the Year award. James Tomlinson...
WINNER: Comodo - ESM Comodo won the Anti Malware Solution of the Year award. James Tomlinson...
Network Security Solution of the Year 2014
WINNER: Fortinet - Fortigate 1500D
WINNER: Fortinet - Fortigate 1500D
Identity and Access Management Solution of the Year 2014
WINNER: Celestix - HOTPin
WINNER: Celestix - HOTPin
SIEM (Security Incident and Event Management)...
WINNER: RSA - Security Analytics
WINNER: RSA - Security Analytics
Network Access Control Solution of the Year 2014
WINNER: Vasco - Digipass
WINNER: Vasco - Digipass
Encryption Solution of the Year - Security 2014
WINNER: Egress Software Technologies - Egress Switch
WINNER: Egress Software Technologies - Egress Switch
DLP Solution of the Year - Security 2014
WINNER: CoSoSys - Endpoint Protector 4
WINNER: CoSoSys - Endpoint Protector 4
Mobile Security Solution of the Year - Security 2014
WINNER: Palo Alto Networks - GP 100
WINNER: Palo Alto Networks - GP 100
Cloud Security Solution of the Year - 2014
WINNER: Assuria - Assuria Log Manager MSP
WINNER: Assuria - Assuria Log Manager MSP
Messaging Security Solution of the Year 2014
WINNER: Voltage Security - SecureMail
WINNER: Voltage Security - SecureMail
Advanced Persistent Threat (APT) Solution of the Year...
WINNER: WatchGuard - WatchGuard APT Blocker
WINNER: WatchGuard - WatchGuard APT Blocker
Fraud Prevention Award - Security 2014
WINNER: ZeroDayLab
WINNER: ZeroDayLab
Security Service Provider of the Year 2014
WINNER: Nettitude
WINNER: Nettitude
SME Security Solution of the Year 2014
WINNER: Halon Security - Halon Email Security
WINNER: Halon Security - Halon Email Security
Enterprise Security Solution of the Year 2014
WINNER: CyberArk - Privileged Account Security Solution
WINNER: CyberArk - Privileged Account Security Solution
Security Project of the Year 2014
WINNER: SThree/Good Technology
WINNER: SThree/Good Technology
Editor’s Choice - Security 2014
WINNER: Cyberoam - CR35iNG
WINNER: Cyberoam - CR35iNG
Security Distributor of the Year 2014
WINNER: Wick Hill
WINNER: Wick Hill
Security Reseller of the Year 2014
WINNER: Brookcourt Solutions
WINNER: Brookcourt Solutions
New Product of the Year - Security 2014
WINNER: Wallix - WAB On Demand
WINNER: Wallix - WAB On Demand
Personal Contribution to IT Security Award 2014
WINNER: Ian Whiting - Titania
WINNER: Ian Whiting - Titania
Security Company of the Year 2014
WINNER: Celestix
WINNER: Celestix
Securing the honours!
It was another night of celebrations at the 2013 Computing Security Awards, as people from right across the industry gathered..
It was another night of celebrations at the 2013 Computing Security Awards, as people from right across the industry gathered..
Celebration - and jubilation!
It was another night of huge celebrations at the 2013 Computing Security Awards, as people from right across the industry...
It was another night of huge celebrations at the 2013 Computing Security Awards, as people from right across the industry...
Security - Anti Spam Solution of the Year 2013
WINNER: Kaspersky Lab - Endpoint Security for Business...
WINNER: Kaspersky Lab - Endpoint Security for Business...
Security - Anti Malware Solution of the Year 2013
WINNER: Cloudmark - Server Edition..
WINNER: Cloudmark - Server Edition..
Security - Content Security Solution of the Year 2013
WINNER: Check Point - Application Control Software Blade..
WINNER: Check Point - Application Control Software Blade..
Network Security Solution of the Year 2013
WINNER: Emulex - EndaceProbe
WINNER: Emulex - EndaceProbe
Sparkling outcome!
A solution from Libraesva is enabling private wine house Casa Vinicola Zonin to protect the 250 mailboxes of its internal...
A solution from Libraesva is enabling private wine house Casa Vinicola Zonin to protect the 250 mailboxes of its internal...
Game on!
Games Workshop found that the value of its electronic communications was being severely eroded by a deluge of spam,....
Games Workshop found that the value of its electronic communications was being severely eroded by a deluge of spam,....
Complying with current and potential future changes to...
This paper reviews one critical area of data protection, ICT disposal, looks at the likely impact...
This paper reviews one critical area of data protection, ICT disposal, looks at the likely impact...
Managing End of Life Risk For Solid State Devices (SSD)
Devices that use SSD face many challenges when they reach their end of life, especially around...
Devices that use SSD face many challenges when they reach their end of life, especially around...
Forensic Analysis of Factory Reset Function as a permissible...
This paper examines the assertion that the factory reset function as specified and supported...
This paper examines the assertion that the factory reset function as specified and supported...
Meeting European Data Protection and Security Requirements...
This white paper investigates how encryption and tokenisation of data can help companies that are subject both to EU data protection...
This white paper investigates how encryption and tokenisation of data can help companies that are subject both to EU data protection...
How to avoid a tangled Web
Web 2.0 aids enterprises in conducting business, but also introduces many damaging risks. Trend Micro offers its insights into Web application vulnerabilities and how to avoid these...
Web 2.0 aids enterprises in conducting business, but also introduces many damaging risks. Trend Micro offers its insights into Web application vulnerabilities and how to avoid these...
'2014: The Danger Deepens'
Neustar has released its 'Annual United Kingdom DDoS Attacks & Impact Report'. What were the experiences of those surveyed in 2013?....
Neustar has released its 'Annual United Kingdom DDoS Attacks & Impact Report'. What were the experiences of those surveyed in 2013?....
Inside the criminal mind
Infoblox has launched a whitepaper that takes a sideways look at DNS security from the perspective of a cybercriminal
Infoblox has launched a whitepaper that takes a sideways look at DNS security from the perspective of a cybercriminal
AIIM survey into digital signatures
"Digital Signatures - making the business case"
"Digital Signatures - making the business case"
Secure Mobile Workflows
The majority of employees now demand their choice of apps, collaboration spaces, and cloud storage. Each personalized...
The majority of employees now demand their choice of apps, collaboration spaces, and cloud storage. Each personalized...
'Surely Not' - The Surprising Weakness Of Strong Authentication Technologies
Dr Basil Philipsz outlines vulnerabilities in current Authentication Technologies and explains how his company, Distributed...
Dr Basil Philipsz outlines vulnerabilities in current Authentication Technologies and explains how his company, Distributed...
Cloud-based services: Easing the IT burden while taking control
As mobile device management becomes an ever greater challenge, its convergence with two-factor authentication...
As mobile device management becomes an ever greater challenge, its convergence with two-factor authentication...